There's quite a difference between 10.1.4.1 (and earlier versions) and 10.1.4.3 in the syncing business. You may now use multiple profiles quite easily and even have separate jobs for each profile. This would allow for a multi-AD-domain company to allow for different frequencies of synchronization: have one, well-know busy AD Domain synchronize very frequently, and other less frequent.
You may also enable or disable profiles by simply removing them from the running sync job(s); that process is called disassociation.
Receipe
So, what do I need?
1 Active Directory Installation
1 Oracle Identity Management Installation
I go both, one running VMWare (MS AD - I had it shipped as VMWare image), one Oracle, installed under VirtualBox.
Start it up
As the Oracle installation is as basic as it can be, it needs starting up:
frank@frank-cs03:~$ ssh oracle@192.168.1.222
oracle@192.168.1.222's password:
Last login: Fr Sep 10 16:43:24 2010
[oracle@oracleas ~]$ . oraenv
ORACLE_SID = [oracle] ? iasdb
[oracle@oracleas ~]$ lsnrctl start
LSNRCTL for Linux: Version 10.1.0.5.0 - Production on 29-DEC-2010 09:46:40
Copyright (c) 1991, 2004, Oracle. All rights reserved.
Starting /oracle/ias/10.1.4/bin/tnslsnr: please wait...
TNSLSNR for Linux: Version 10.1.0.5.0 - Production
System parameter file is /oracle/ias/10.1.4/network/admin/listener.ora
Log messages written to /oracle/ias/10.1.4/network/log/listener.log
Listening on: (DESCRIPTION=(ADDRESS=(PROTOCOL=tcp)(HOST=oracleas)(PORT=1521)))
Listening on: (DESCRIPTION=(ADDRESS=(PROTOCOL=ipc)(KEY=EXTPROC1521)))
Connecting to (DESCRIPTION=(ADDRESS=(PROTOCOL=TCP)(HOST=oracleas)(PORT=1521)))
STATUS of the LISTENER
------------------------
Alias LISTENER
Version TNSLSNR for Linux: Version 10.1.0.5.0 - Production
Start Date 29-DEC-2010 09:46:41
Uptime 0 days 0 hr. 0 min. 0 sec
Trace Level off
Security ON: Local OS Authentication
SNMP OFF
Listener Parameter File /oracle/ias/10.1.4/network/admin/listener.ora
Listener Log File /oracle/ias/10.1.4/network/log/listener.log
Listening Endpoints Summary...
(DESCRIPTION=(ADDRESS=(PROTOCOL=tcp)(HOST=oracleas)(PORT=1521)))
(DESCRIPTION=(ADDRESS=(PROTOCOL=ipc)(KEY=EXTPROC1521)))
Services Summary...
Service "PLSExtProc" has 1 instance(s).
Instance "PLSExtProc", status UNKNOWN, has 1 handler(s) for this service...
The command completed successfully
I need a tcp based listener, because of the OID/ldap stack, that uses tcp. Otherwise, I would not have gone through all of the tcp stack, but use Direct Calls, or even better: bequeth, which does not need a listener at all. Anyway - open the database:
[oracle@oracleas ~]$ sqlplus / as sysdba
SQL*Plus: Release 10.1.0.5.0 - Production on Wed Dec 29 09:47:33 2010
Copyright (c) 1982, 2005, Oracle. All rights reserved.
Connected to an idle instance.
SQL> startup
ORACLE instance started.
Total System Global Area 281018368 bytes
Fixed Size 779000 bytes
Variable Size 229645576 bytes
Database Buffers 50331648 bytes
Redo Buffers 262144 bytes
Database mounted.
Database opened.
SQL> exit
Disconnected from Oracle Database 10g Enterprise Edition Release 10.1.0.5.0 - Production
With the Partitioning, OLAP and Data Mining options
After all that, it is time to get ldap running. It needs to connect to the database, so this is the correct starting order:
[oracle@oracleas ~]$ $ORACLE_HOME/opmn/bin/opmnctl startall
opmnctl: starting opmn and all managed processes...
See if all is started:
[oracle@oracleas ~]$ $ORACLE_HOME/opmn/bin/opmnctl status
Processes in Instance: ias_1014.oracleas
-------------------+--------------------+---------+---------
ias-component | process-type | pid | status
-------------------+--------------------+---------+---------
DSA | DSA | N/A | Down
LogLoader | logloaderd | N/A | Down
dcm-daemon | dcm-daemon | N/A | Down
OC4J | OC4J_SECURITY | 2811 | Alive
HTTP_Server | HTTP_Server | 2726 | Alive
OID | OID | 2731 | Alive
If you would like to know which ports are used by the http server, use the "-l" option of the opmnctl command (-l stands for "long").
Now, with the OID, there's another check you ought to be aware of. Similar to the way the Oracle Process Manager (opmn) monitors, OID has it's own set of monitors. Activity of these can be checked by using the ldapcheck command:
[oracle@oracleas ~]$ $ORACLE_HOME/ldap/bin/ldapcheck
Checking Oracle Internet Directory Processes ...ALL
Process oidmon is Alive as PID 2731
Process oidldapd is Alive as PID 2749
Process oidldapd is Alive as PID 2783
Not Running ---- Process oidrepld
Process odisrv is Alive as PID 2770
oidmon (PID 2731) is the OID Monitoring process itself; it is the process, that is actually monitored by opmn. The two oidldapd processes are two LDAP Daemons. Other than that, there's an inactive Replication process, oidrepld, that is only used in Enterprise-class setups, as I
described here.The final process is the one, I'm interested in: it's the Oracle Directory Integration service, odisrv for short.
What if I have no ldapcheck?
Well, I did not, either. You can download
diptester from here, unzip it, and rename "ldapcheck_for_HPUX" to ldapcheck, do a chmod 740, and you're in business.
What id ldapcheck returns
ps: illegal option -- o
Apply same medicin as "What if I do not have ldapcheck"
Synchronize!
Now, in order to get OID to synchronize from AD, I need a few things:
- a highly privileged account on Active Directory
- Names, or IP-addresses, of servers involved
- an understanding of mapping, with base of OID as well as AD
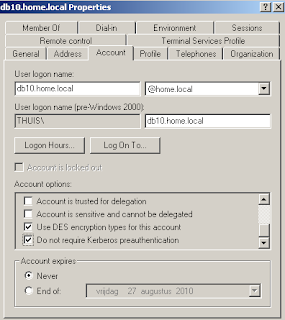
As for the account, I'll use my own account, which is member of the administrators group - do not use this in production! But you do need an account, that is allowed to query the "Deleted users" section - and that requires quite some privileges. If you cannot see "Deleted Users", users can be removed from AD, but will always remain in OID. And that is a security issue...
IP addresses: The oracle iAS runs is called oracleas.home.local at 192.168.1.222, the PDC is located at 192.168.1.233.
Mapping: well, whoever invented that should be prosecuted. As long as you keep it basic, and simple, there are few problems. As soon as you company is operating multiple domains, it is a RPITA to get things running smoothly.
Profiles
Mapping is based on profiles. The fastest way to get things running is to take a copy of $ORACLE_HOME/ldap/odi/conf/activechg.map.master and use that as basis.
The base in OID is dc=bortel,dc=home, as you can see from this picture of the OID Aministration tool, oidadmin:

This is the correct entry, as this entry holds the users. Same is true for Active Directory, although I know no other way than to query the darn thing:
C:\Documents and Settings\frank>ldapsearch -Z -h w2k-pdc -p 3268 cn=frank cn
CN=frank,CN=Users,DC=home,DC=local
cn=frank
What I am doing here, is query my own credentials, using the built-in security (-Z), the localhost as ldap host (-h w2k-pdc), and query the Global Catalog port (-p 3268).
Anyway - my AD mapping is dc=home, dc=local.
Mapping rules
In the mapping file, this results in the first line being:
cn=users,dc=home,dc=local:cn=users,dc=bortel,dc=home
In words: maps everything, found under cn=users,dc=home,dc=local (in Active Directory, as it is left of the colon) to cn=users,dc=bortel,dc=home (in Oracle Internet Directory, as it is right of the colon).
These are the domain rules.
If you have more domains, just add mapping rules. If you have organized your domain in Units (Organizational Units, or "ou" in LDAP-speak), start mapping rules at that level, and add, or omit to your needs.
dipadmin
Now, a new tool needs to be used, the dispassistant. User is dipadmin - password of dipadmin is identical to the password of orcladmin:

New in this version is the use of Connector Profiles, and profile Sets.
Due to badly documented features, and some documentation bugs it is best to create a new Connector Group.
First of all, rename the Connector Groups "configset1" to "standardgroup". The original name will just create misunderstanding, as the are configsets in use with OID.

Then, create the group you will be using for your actions - the "standardgroup" will remain as the group holding all defaults, but will not actually be used. My new group is called "demo":

Next, go to the standardgroup, and disassociate ActiveChgImp:

Then, select the newly created group "demo", and associate the profile:

Note, the profile is still Disabled. Edit the profile, and fill in the connection defaults on the first tab:

On the third tab, make sure the filter properties do not have quotes around them - it's a bug:

On the last tab, I always change "Continue on Error" to Yes; I have no tools to monitor whether every change gets into OID correctly. Most of the errors I see, are on duplicated entries anyway.
You may also want to change the frequency of synchronization: every 60 seconds seems on the high side, escpecially if you have 7 profiles, like my customer, one of which connects to a Active Directory with 13,000 users.

Modify the profile mapping file to your liking, and load it into the profile:
[oracle@oracleas ~]$ dipassistant mp -D cn=orcladmin -profile=activechgimp odip.profile.mapfile=demo_user.map
Password:
Profile successfully modified.
[oracle@oracleas ~]$
Bootstrap
The first, initial (bulk) load of the accounts is call bootstrapping:
[oracle@oracleas ~]$ dipassistant mp -D cn=orcladmin -profile=activechgimp odip.profile.mapfile=demo_user.map
Password:
Profile successfully modified.
[oracle@oracleas ~]$
Results of this process may be found in $ORACLE_HOME/ldap/odi/log/bootstrap.log and ~.trc
You can also inspect the OID with the oidadmin tool:

(and see there's a problem with krbPrincipalName...)
Activate
Now, all that's left is to start the process of syncs every x seconds. In order to do that, I'll need to start the connectorgroup:
[oracle@oracleas ~]$ $ORACLE_HOME/ldap/bin/ldapcheck
Checking Oracle Internet Directory Processes ...ALL
Process oidmon is Alive as PID 2513
Process oidldapd is Alive as PID 2519
Process oidldapd is Alive as PID 2526
Not Running ---- Process oidrepld
Process odisrv is Alive as PID 2521
[oracle@oracleas ~]$ oidctl connect=iasdb server=odisrv instance=2 configset=1 flags="grpid=demo" start
NLS_LANG not set in environment
Setting NLS_LANG to AMERICAN_AMERICA.AL32UTF8
oidctl:Waiting for oidmon to start ODISRV (instance=2)
oidctl:Waiting for oidmon to start ODISRV (instance=2)
oidctl:Started ODISRV (instance=2) with PID : 21496 successfully
[oracle@oracleas ~]$ $ORACLE_HOME/ldap/bin/ldapcheck
Checking Oracle Internet Directory Processes ...ALL
Process oidmon is Alive as PID 2513
Process oidldapd is Alive as PID 2519
Process oidldapd is Alive as PID 2526
Not Running ---- Process oidrepld
Process odisrv is Alive as PID 2521
Process odisrv is Alive as PID 21496
[oracle@oracleas ~]$
There are two odi processes now. The second one is the AD-OID synchronisation.
Logging of this process is in the same directory as the bootstrap: $ORACLE_HOME/ldap/odi/log.
You will see the timestamp changing (and the file will grow.
Now, after adding a new user in AD, I can quey these:
[oracle@oracleas ~]$ ldapsearch cn=frank* uid
cn=frank,cn=users,dc=bortel,dc=home
cn=frank w.j.. van bortel,cn=users,dc=bortel,dc=home
uid=frank2@home.local
And that proves, the synchronisation is working!
Groups, and all that
This is to be added: how to sync groups, and split these. I will also mention some considerations about syncing, especially on multiple domains.